CVE-2023-44487 HTTP/2 Rapid Reset Attack
Today, Amazon Web Services, Cloudflare, and Google, in a coordinated announcement, reveal their experiences mitigating powerful HTTP/2-based DDoS attacks utilizing a zero-day technique referred to as ‘Rapid Reset’, documented under the vulnerability identifier CVE-2023-44487. The attack magnitudes reported are astonishing: Amazon mitigated attacks at a rate of 155 million requests per second, Cloudflare at 201 million rps, and Google endured a record-breaking 398 million rps. This vulnerability was under active attack in August.
What is CVE-2023-44487 HTTP/2 Rapid Reset Attack?
The ‘Rapid Reset’ technique leverages the ‘stream multiplexing’ feature of HTTP/2, wherein numerous requests and subsequent immediate cancellations cause substantial server-side workload with minimal client-side attacker cost. The attack takes advantage of a feature in HTTP/2 by repeatedly sending and canceling requests, which overwhelms the target website or application, causing it to stop working correctly. HTTP/2 has a safety feature that tries to limit the number of active streams to protect against DoS attacks, but it doesn’t always work effectively. The protocol allows the client to cancel streams without needing the server’s agreement, which is exploited in this attack. Botnets can generate massive request rates, posing a severe threat to targeted web infrastructures.
Considering the CVE-2023-44487 vulnerability, which affects web servers by causing additional load through rapid stream generation and cancellation, potentially leading to a Denial of Service. Customers utilizing their own HTTP/2-enabled web servers are encouraged to communicate with their respective web server vendors to implement necessary patches as needed.
What should organizations do?
In mitigating HTTP/2 Rapid Reset attacks, a multi-faceted approach is essential. Utilize comprehensive HTTP-flood protection tools and enhance DDoS defenses by employing various mitigative strategies. Implementing rate controls is pivotal in managing the effects of the attacks since they exploit the protocol directly and lack a one-size-fits-all solution. Critically, the underpinning preventive measure across all defenses is the vital and timely updating and patching of systems. Customers should update their systems with available patches to strengthen against this vulnerability, ensuring a robust barrier against exploitative attacks.
How can Qualys Help?
Addressing the risks of CVE-2023-44487, or the HTTP/2 Rapid Reset Attack, starts with identifying vulnerable assets. Utilize the following QIDs to aid this matter.
| QID | Title | VulnSigs Version |
| 45475 | Apache http2 module Detected | VULNSIGS-2.5.87.2-1 |
| 45266 | Web Server HTTP Protocol Versions | VULNSIGS-2.4.25-2 |
| 92067 | Microsoft HTTP/2 Protocol Distributed Denial of Service (DDoS) Vulnerability | VULNSIGS-2.5.884-3 |
| 92070 | Microsoft Azure Stack Hub Security Updates for October 2023 | VULNSIGS-2.5.884-3 |
| 150732 | Apache Tomcat Multiple Vulnerabilities (CVE-2023-42795, CVE-2023-44487, CVE-2023-45648) | VULNSIGS-2.5.889-3 |
Evaluate Vendor-Suggested Mitigation with Policy Compliance (PC)
With Qualys Policy Compliance’s Out-of-the-Box Mitigation or Compensatory Controls reduce the risk of a vulnerability being exploited because the remediation (fix/patch) cannot be done now, these security controls are not recommended by any industry standards such as CIS, DISA-STIG.
Qualys Policy Compliance team releases these exclusive controls based on Vendor-suggested Mitigation/Workaround.
Mitigation refers to a setting, common configuration, or general best practice, existing in a default state, that could reduce the severity of exploitation of a vulnerability.
A workaround is a method, sometimes used temporarily, for achieving a task or goal when the usual or planned method isn’t working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned.
The following Qualys Policy Compliance Control IDs (CIDs), and System Defined Controls (SDC) have been updated to support recommended mitigation(s):
For Windows and IIS technology:
- 17331 Status of the ‘HTTP/2’ feature on the host (EnableHttp2Cleartext)
- 17330 Status of the ‘HTTP/2’ feature on the host (EnableHttp2Tls)
For F5 BIG-IP technology:
- 26840 Status of the ‘concurrent-streams-per-connection’ setting configured for the ltm http2 profile
For Nginx technology:
- 26842, Status of the ‘http2_max_concurrent_streams’ setting (Http Block)
- 26844, Status of the ‘http2_max_concurrent_streams’ setting (Server Block)
- 26841, Status of the ‘keepalive_requests’ setting (Http Block)
- 26843, Status of the ‘keepalive_requests’ setting (Server Block)
- 26845, Status of the ‘keepalive_requests’ setting (location block)
- 22615, Status of the ‘limit_conn’ setting (Http Block)
- 22616, Status of the ‘limit_conn’ setting (Server Block)
- 22617, Status of the ‘limit_conn’ setting (Location Block)
- 22619, Status of the ‘limit_req’ setting (Http Block)
- 22620, Status of the ‘limit_req’ setting (Server Block)
- 22621, Status of the ‘limit_req’ setting (Location Block)
For Citrix NetScaler technology:
- 26904 Status of HTTP2 Maximum Concurrent Streams
- 26905 Status of Max Conn for every service configured
- 26906 Status of HTTP2 on Http profile
Execute Mitigation Using Qualys Custom Assessment and Remediation (CAR)
Qualys Custom Assessment and Remediation (CAR) can be leveraged to execute mitigation.
For Windows and IIS technology
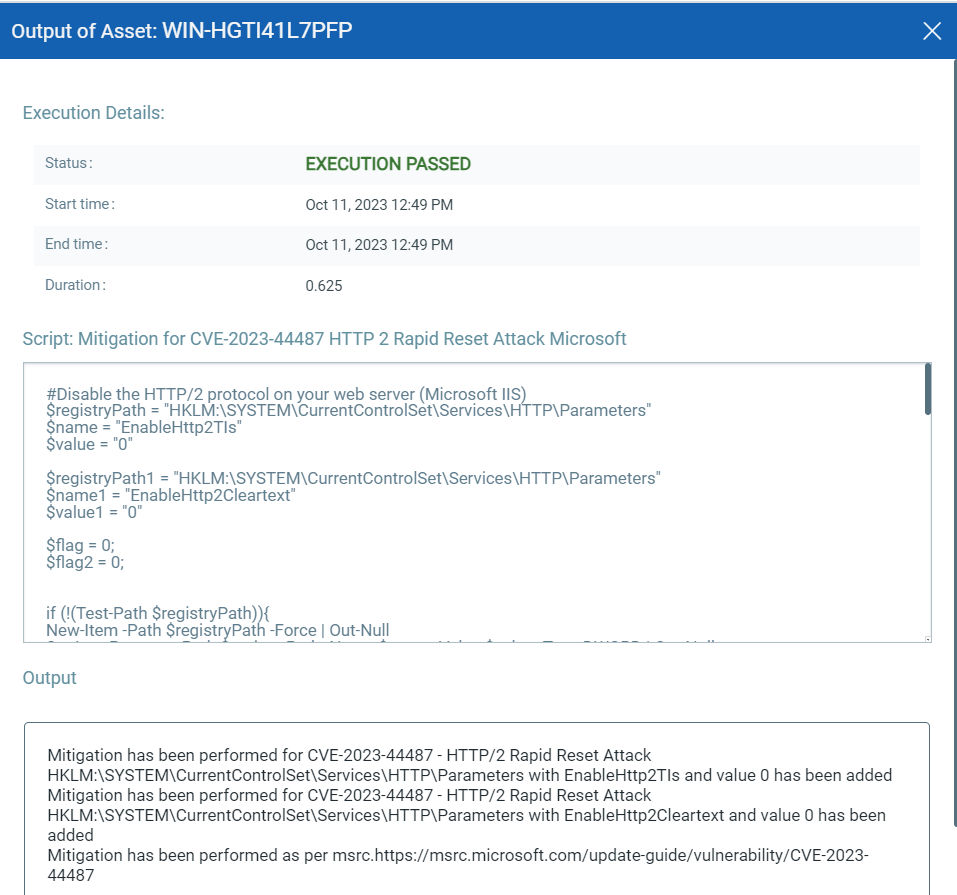
CAR team is addressing the introduced mitigation/workaround from other supported technologies and will provide an update once scripts are added to the library.
Note: Scripts will be available in the CAR script library.
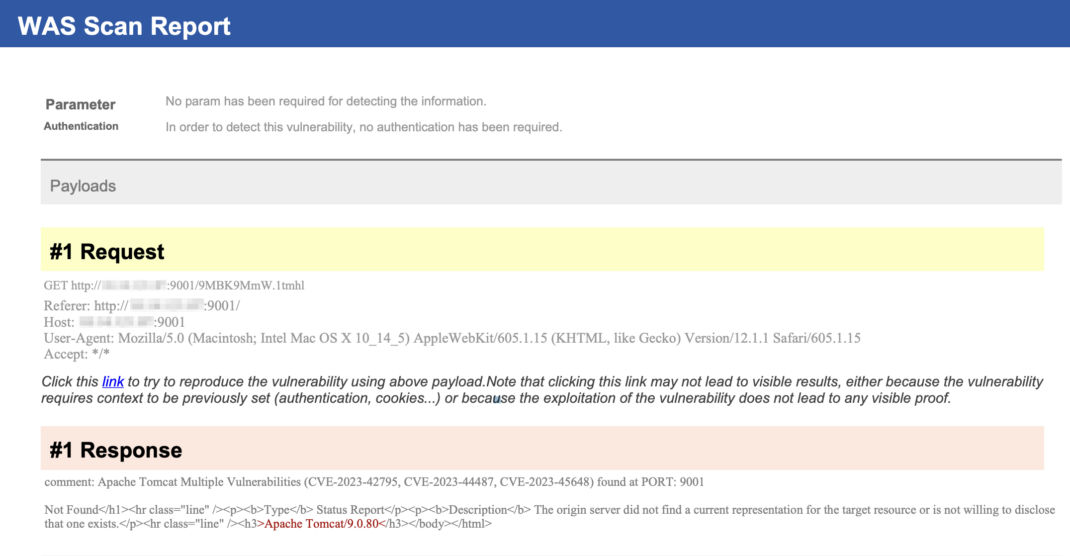
Detecting Vulnerability with Qualys WAS
Customers can launch WAS scan and if their Apache tomcat servers are vulnerable, QID 150732 will be reported. The QID is detected based on installed version.
The information below showcases the HTTP request and response used to identify the above-mentioned vulnerability. This detection was made possible using the Qualys Web Application Scanning (WAS) system, specifically with the QID 150732.
Conclusion
This story is still unfolding. The Qualys Threat Research Unit remains proactive, with additional QIDs to be released. Stay tuned for subsequent updates. In response to the CVE-2023-44487 HTTP/2 ‘Rapid Reset’ attack, urgent patching is essential. Organizations must prioritize immediate system updates, ensuring protection against these notably disruptive cyber threats.
Additional Contributors:
- Xiaoran (Alex) Dong, Manager, Compliance Signature Engineering, Qualys
- Sheela Sarva, Director, Quality Engineering, Web Application Security, Qualys